Every fifth owner of a personal computer has been attacked by scammers on the World Wide Web. A popular type of deception are Winlocker Trojans - these are banners that block Windows work processes and require you to send an SMS to a paid number. To get rid of such ransomware, you need to figure out what threats it poses and how it gets into the system. In particularly difficult cases, you will have to contact the service center.
How do virus banners get onto a computer?
First on the list of sources of infection are pirated programs for work and leisure. We must not forget that Internet users have become accustomed to obtaining software online for free. But downloading software from suspicious sites carries a high risk of banner infection.
Windows often locks when opening a downloaded file with the “.exe” extension. Of course, this is not an axiom; it makes no sense to refuse to download software with such an extension. Just remember a simple rule - “.exe” is a game or program installation extension. And its presence in the name of video, audio, image or document files maximizes the likelihood of a computer being infected by a Winlocker Trojan.

The second most common method is based on a call to update your flash player or browser. It looks like this: when moving from page to page while surfing the Internet, the following message pops up - “your browser is out of date, install an update.” Such banners do not lead to the official website. Agreeing to an upgrade offer from a third-party resource will in 100% of cases lead to infection of the system.

How to remove banner ransomware from your computer
There is only one way with a 100% guarantee - reinstalling Windows. The only downside here is a very big one - if you do not have an archive of important data from the C drive, then during a standard reinstallation they will be lost. Are you eager to reinstall programs and games because of the banner? Then it’s worth taking note of other methods. They all fall into two main categories:
- There is access to safe mode;
- You cannot use Safe Startup mode.
Viruses are constantly being improved and can disable any OS boot mode. Therefore, the first option to remove the banner from your computer is not always possible.
With all the variety of methods of pest control, all operations come down to one principle. After the removal procedure is completed and the system is successfully rebooted (when there are no ransomware banners), additional measures are required. Otherwise, the virus will appear again, or the computer will freeze. Let's look at the two most common ways to avoid this.
Safe mode
Reboot the computer by pressing the F8 key until a menu of other OS boot options appears. In it, using the arrows on the keyboard, select the line “Safe Mode with Command Line Support” from the list.

If the malware has not penetrated deeply into the system, the desktop will be displayed. Through the “Start” button, select “Search files and programs.” In the window that appears, fill in the “regedit” command. Here you will need basic knowledge of computer systems to clean the registry of the virus and remove its consequences.

Let's start with the directory:
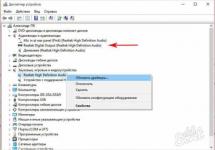
HKEY_LOCAL_MACHINE\Software\Microsoft\WinNT\CurrentVersion\Winlogon. In it we study 2 subparagraphs sequentially. Shell - only the “explorer.exe” item should be present. Other values - a sign of a banner - are deleted. Userinit should contain "C:\Windows\system32\userinit.exe". Instead of the letter “C” there may be another one if the operating system is running from a different local drive.

- HKEY_CURRENT_USER (similar subdirectories). If the sub-items listed above are present, they must be deleted.
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run. All suspicious lines with meaningless names must be cleared - for example, “skjgghydka.exe”. Do you have any doubts about the harm of the registry file? In fact, the removal process is not necessary. Add "1" to the beginning of its name. Having an error, it will not start, and if necessary, you can return the original value.
- HKEY_CURRENT_USER (subdirectories). Actions are the same as in the previous paragraph.
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunOnce. We repeat all operations.
- HKEY_CURRENT_USER (further path, as in the paragraph above). We are carrying out similar actions.
After completing all the steps, run the system utility “cleanmgr”. Having selected a local drive with Windows, we start scanning. Next, in the window that appears, check all the boxes except “Update package backup files.” After running the utility, all that remains is to clean and remove the consequences of the virus.

Restoring the system to a checkpoint
To remove the banner from the computer, we will use a standard system restore to the existing save point that preceded the appearance of the Winlocker. The process is started via the command line by entering the value "rstrui". In the window that opens, you can select a recommended date or set your own from the available list.

The recovery will take some time and will end with a system reboot. The result will be complete removal of the malicious program. In some cases, a message may appear indicating that it is impossible to restore the system. With this option, all you have to do is contact the service center. It’s better to do this if you don’t have the necessary skills to work with the registry.
Protect your computer from being blocked
Anyone can encounter a Winlocker Trojan. It’s easy to avoid a nervous situation if you follow simple safety rules:
- Install a working antivirus program;
- Do not open suspicious emails;
- Do not click on pop-up messages on the Internet;
- Update your operating system regularly.
But if trouble has already arisen, the Recomp service center will help you. Our specialists will remove blocking programs and other viruses, eliminate traces of their presence and improve the operation of the operating system. With us it is easy to avoid the loss of important data, and if necessary, we will restore lost files!
For free
For free
Banner ransomware is a special viral program that completely blocks access to controls of the Windows operating system in order to extort money for unlocking access by sending money to the phone number or e-wallet of the attackers. Despite the fact that the main wave of the influx of virus banners passed a couple of years ago, we still periodically have to deal with cases of computers being damaged by this dirty trick. This mainly happens to users who have not bothered to protect their PC from viruses. If you do not have a normal antivirus installed, then one day, instead of your usual desktop, you will see a banner that, in order to be deleted, will require you to send an SMS to your mobile phone number, supposedly to receive an unlock code. This is a complete deception and no matter how much money you send, of course there will be no answer! Now I will give 3 ways to remove ransomware banner from a Windows computer. If they do not help, then only a complete reinstallation of the operating system will help.
There are 3 ways in which you can remove a banner in Windows:
The first way to remove a banner
Try using your phone, tablet or other computer to search the Internet for the unlock code using your phone number. Code generators for unlocking ransomware viruses are posted on the websites of the largest companies developing anti-virus software. For example, Kaspersky Lab, DrWeb and Deblocker. There, you usually need to enter a phone number to which the attackers demand you send money and SMS, or an e-wallet number. In response to this, you will receive a code that will help you deactivate the blocker.
The only unpleasant thing is that this method works on the oldest and simplest ransomware banners. On a more cunning, complex and advanced “infection” this trick no longer works and to treat it you will need to use the following two methods.
The second way to unblock a banner on your computer
Use the Kaspersky WindowsUnlocker utility from Kaspersky Lab.

It is included in Kaspersky Rescue Disk. This is an excellent free tool that will help you quickly and easily remove banner ransomware virus from your Windows 10 computer.
The third way to remove a Windows blocker virus
1. You need to boot the system in safe mode. In Windows 7, you need to press the F8 button at startup to do this. In Windows 10 or Eight, you will need an installation disk or flash drive. More details are well written in the article Windows 10 Safe Mode.
2. Next, you need to open the registry editor. To do this, press the Win+R key combination and enter the command in the “Run” window regedit.
3. In the registry editor we find the branch:
HKEY_LOCAL_MACHINE\ SOFTWARE\ Microsoft\ Windows NT\ CurrentVersion\ Winlogon
It will contain the entry “Shell”. Double-click on it and register the standard Windows Explorer - explorer.exe
If the explorer is already registered in the “Shell” entry, then open the branch:
HKEY_LOCAL_MACHINE\ SOFTWARE\ Microsoft\ Windows NT\ CurrentVersion\ Image File Execution Options
Unfold it and study it carefully. If there is a subsection “explorer.exe” there, simply delete it by right-clicking and selecting the “Delete” menu item.
4. Reboot the computer. Windows should boot normally. After this, be sure to check your computer with a good antivirus. For example, free DrWeb CureIT.
- Disabling unnecessary Windows services to improve...
Often, users become victims of viruses that seriously interfere with working in Windows. A striking example is blocking the desktop using a banner. This happens if you haven't taken care of protecting your computer. You cannot perform any actions, the OS is locked, and the screen says something like “You have broken the law. Top up such and such a mobile number, otherwise you will lose all your data.” This article describes how to remove such a banner from the desktop of your computer. 
Please understand that this is a scam. You didn’t violate anything; there are no provisions in the law regarding blocking users’ desktops. Under no circumstances follow the lead of scammers and do not send them your money.
Most likely, this will not even help - unlocking using a code is unlikely to help get rid of the virus, and the banner will remain on the computer.
Often, to get rid of such problems, it is recommended to simply reinstall the operating system. Of course, uninstalling and reinstalling Windows will definitely help. But this is a long way. Don't forget that you still need to install all the necessary drivers and programs.
This article discusses simpler and faster ways to get rid of ransomware banners.
Starting in Safe Mode
If you find that when you start Windows, a banner pops up that blocks all functions of the computer, you need to start the operating system in diagnostic mode. To do this, follow the instructions provided:

This will take you to Windows diagnostic mode. If you succeeded and the banner is not here, move on to the next part of the guide. If there is a lock in this mode, you will need to start the PC using LiveCD (described below).
Typically, a banner virus modifies some entries in the registry, which causes Windows to malfunction. Your task is to find all these changes and eliminate them.
Editing the Registry
Open the Run dialog using the Win + R key combination. In the window that opens, enter the command “regedit” and press Enter. You will be taken to the Windows Registry Editor. Follow the instructions carefully so you don't miss anything. 
Using the directory on the left side of the program window, users need to open the following directories:
· HKEY_LOCAL_MACHINE/Software/Microsoft/Windows/Current Version/Run
Here you need to find the entry responsible for autorunning your banner when the system starts. Next, it should be removed. Right-click on the entry and select the “Delete” option from the context menu that opens. Feel free to delete anything suspicious; it will not affect the operation of your system in any way. If you delete something unnecessary, such as Skype autostart, you can get everything back. 
· HKEY_LOCAL_MACHINE/Software/Microsoft/Windows NT/CurrentVersion/Winlogon
In this folder you need to find a parameter called “Shell” and assign it the value “explorer.exe”. Next, find the “Userinit” entry and give it a value "C:\Windows\system32\userinit.exe". To edit entries, simply double-click on them. 
· HKEY_CURRENT_USER/Software/Microsoft/Windows NT/CurrentVersion/Winlogon
Also look for the "Userinit" and "Shell" options. Write down their meanings somewhere - these are the paths to your banner. Delete both entries. They shouldn't be in this directory.
Prevention
Once you have managed to remove all unnecessary entries from the Windows registry, you can close the editor and restart your computer. The system should start without any problems.
Now you need to remove the “tails” that are left from the malicious script. Open Windows Explorer (My Computer). Find the files that were referenced by the "incorrect" Shell and Userinit parameters and delete them.
After this, it is very important to scan the system using an antivirus program. Preferably with the deepest scan available in your antivirus. If you do not have any system protection, download and install immediately. For example, you can use a free program from Microsoft - Security Essentials. You can download it from this link - https://www.microsoft.com/ru-ru/download/details.aspx?id=5201.
 The following guide describes how to remove the banner if it opens even while starting Windows Safe Mode.
The following guide describes how to remove the banner if it opens even while starting Windows Safe Mode.
Creating a Live CD from Kaspersky
If you are unable to remove the banner through safe mode, you should use a LiveCD. This is a special mini-OS that is recorded on a disk or flash drive. With it, you can boot up and edit a damaged registry or run an automatic troubleshooting utility.
For example, you can use a free service from Kaspersky Lab. To do this, you need to create a bootable USB flash drive or disk on another, working computer:

Unlocking via Kaspersky Live CD
To remove the effects of virus infection, you will need to do the following:

Installation disk
You can also use the installation disk from your operating system to get rid of the consequences of virus infection. You have to resort to this when the banner appears immediately after the BIOS beep, and you do not have the opportunity to use other means.
Insert the installation disk or bootable USB flash drive with an image of your system and restart the PC. Call the Boot Menu and select boot from external media. If necessary, press any key on the keyboard. Next, removing the consequences of a virus attack is described using Windows 7 as an example.
Select the interface language and click “Next”. At the bottom of the screen, click on the hyperlink "System Restore". A new window will open in which you will need to select "Command line". 
In the console that opens, enter the command “bootrec.exe /FixMbr” and press Enter. After that, enter another command - “bootrec.exe /FixBoot” and press Enter again. Also enter the line “bcdboot.exe c:\windows” (If the system is installed on a different drive, you need to specify it). Reboot your PC and the problem will be solved.
After restarting the computer, the monitor displays a request to send a paid SMS, or to deposit money into a mobile phone account?
Meet this, this is what a typical ransomware virus looks like! This virus comes in thousands of different forms and hundreds of variations. However, he is easy to recognize by a simple sign: he asks you to put money (call) on an unfamiliar number, and in return promises to unlock your computer. What to do?
First, realize that this is a virus whose goal is to suck as much money out of you as possible. That is why do not give in to his provocations.
Remember a simple thing, do not send any SMS. They will withdraw all the money that is on the balance (usually the request says 200-300 rubles). Sometimes they require you to send two, three or more SMS. Remember, the virus will not go away from your computer, whether you send money to scammers or not. Trojan winloc will remain on your computer until you remove it yourself.
The action plan is as follows: 1. Remove the block from the computer 2. Remove the virus and treat the computer.
Ways to unlock your computer:
1. Enter the unlock code And. The most common way to deal with an obscene banner. You can find the code here: Dr.web, Kasperskiy, Nod32. Don't worry if the code doesn't work, move on to the next step.
2. Try booting into Safe Mode. To do this, after turning on the computer, press F8. When the boot options window appears, select “safe mode with driver support” and wait for the system to boot.
2a. Now let's try restore the system(start-standard-system-restore) to an earlier checkpoint. 2b. Create a new account. Go to Start - Control Panel - Accounts. Add a new account and restart the computer. When you turn it on, select the newly created account. Let's move on to .
3. Try ctrl+alt+del- the task manager should appear. We launch healing utilities through the task manager. (select the file - a new task and our programs). Another way is to hold down Ctrl + Shift + Esc and, while holding these keys, search for and delete all strange processes until the desktop is unlocked.
4. The most reliable way- This means installing a new OS (operating system). If you absolutely need to keep the old OS, then we will look at a more labor-intensive way to deal with this banner. But no less effective!
Another way (for advanced users):
5. Booting from disk LiveCD which has a registry editing program. The system has booted, open the registry editor. In it we will see the registry of the current system and the infected one (its branches on the left side are displayed with a signature in brackets).
We find the key HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon - there we look for Userinit - we delete everything after the comma. ATTENTION! The file itself “C:\Windows\system32\userinit.exe” CANNOT be deleted.);
Look at the value of the key HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\Shell it should be explorer.exe. We're done with the registry.
If the error “Editing the registry is prohibited by the system administrator” appears, download the AVZ program. Open "File" - "System Restore" - Check "Unlock Registry Editor", then click "Perform selected operations". The editor is available again.
We launch Kaspersky removal tool and dr.web cureit and scan the entire system with them. All that remains is to reboot and return the bios settings. However, the virus has NOT been removed from the computer yet.
Treating your computer from Trojan WinLock
For this we need:
- ReCleaner registry editor
- popular antivirus Tool removal Kaspersky
- famous antivirus Dr.web cureit
- effective antivirus Removeit pro
- Plstfix registry repair utility
- Program for removing temporary files ATF cleaner
1. It is necessary to get rid of the virus in the system. To do this, launch the registry editor. Go to Menu - Tasks - Launch Registry Editor. Need to find:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon - there we look for the Userinit section - we delete everything after the comma. ATTENTION! The file itself “C:\Windows\system32\userinit.exe” CANNOT be deleted.);
Look at the value of the key HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\Shell there should be explorer.exe. We're done with the registry.
Now select the "Startup" tab. We look through the startup items, check the boxes and delete (lower right corner) everything that you did not install, leaving only desktop and ctfmon.exe. The remaining svchost.exe and other.exe processes from the windows directory must be removed.
Select Task - Clean the registry - Use all options. The program will scan the entire registry and delete everything permanently.
2. To find the code itself, we need the following utilities: Kaspersky, Dr.Web and RemoveIT. Note: RemoveIT will ask you to update the virus signature databases. It is necessary to establish an Internet connection while it is being updated!
With these programs we scan the system disk and delete everything they find. If you wish, you can check all the computer drives just in case. It will take much longer, but it is more reliable.
3. The next utility is Plstfix. It restores the registry after our actions on it. As a result, the task manager and safe mode will start working again.
4. Just in case, delete all temporary files. Often copies of the virus are hidden in these folders. This is how even well-known antiviruses may not detect them. It is better to manually remove anything that will not significantly affect the operation of the system. Install ATF Cleaner, mark everything and delete it.
5. Reboot the system. Everything is working! even better than before :).
In this article I will talk about how to remove porn banner. Most SMS banners and porn banners require you to send an SMS message to a short number and then enter the code received in the response message into the window. If you are reading this text, then it is already clear to you that you should not do this in the future, and the question arises: “How to remove a banner from your computer?”
Problem with porn banners found in the overwhelming majority on Windows XP (but also applies to Windows Vista/7).
Programs for treating and removing porn banners:
AVZ– the utility is designed to detect and remove harmful software:
- SpyWare and AdWare modules are the main purpose of the utility
- Dialer (Trojan.Dialer)
- Trojan programs
- BackDoor modules
- Network and mail worms
- TrojanSpy, TrojanDownloader, TrojanDropper
You can download the AVZ program from .
Malwarebytes- a program for quickly scanning the system to detect and remove various types of malware, including our favorite porn banners. Malwarebytes Anti-Malware is primarily focused on combating spyware modules and allows you to completely restore normal operation of your computer after removing them.
Blocks everything. The unlock code can be found in search engines. We found the deactivation code, entered it and breathed a sigh of relief - the SMS banner disappeared! Now we need to clean the system. There are a great variety of means and ways to do this, you can choose to your taste. Install and scan the system with Malwarebytes’ Anti-Malware, AVZ, then perform a system restore to the point before you caught the banner. Some do not recommend it, but we dare to suggest the ComboFix program (before using it, we highly recommend reading its description). Then go through the program HijackThis, FAV. And finally, any antivirus with updated databases.
If you have not found the unlock code and the SMS banner cannot be deleted:
Kaspersky Rescue CD. Download the iso image, burn it to a disc and boot from it. You launch it. Once the check and treatment are complete, everything should work flawlessly. Reboot and enjoy a clean system.
Unclassified banners
There is another banner that is difficult to classify as any type. The SMS banner blocks almost all simple steps to remove it. Ctrl+Alt+Del doesn't help. Next Ctrl+Esc - the Start Menu appears.
Download the treatment utility AnVir Task Manager.It is not only a modernized alternative to the task manager, but also an antivirus.
Features of AnVir Task Manager
- Managing startup, running processes, services and drivers
- Replacing Task Manager
- Detection and removal of viruses and spyware, blocking attempts to infect the system
- Significant acceleration of Windows loading and computer operation
- The program is completely free
We launch AnVir, go to the Processes tab and calculate our process. In our case it is - services.exe, the process disguised itself as a system service service.exe.
We complete the process and the banner has disappeared. But, although we have a clean desktop in front of us (meaning, without a banner), there is still no Start button on it and the Task Manager does not start. We use a proven method - Ctrl + Esc - Main menu - Programs - Accessories - Explorer.
There is another banner that also does not quite fall into our classification. He is being treated with FAV (FixAfterVirus).
Sometimes, to watch a video, the player requires you to update Flash Player. Here you need to be especially careful. Just after such a notification and subsequent installation of the player, you install the porn banner on your computer. If you pay attention, you will notice differences in the banner style from the original Adobe Flash Player window.
The screensaver that appeared subsequently blocks both regedit and “system restore”, and it is present in SAFE MODE. It does not appear immediately, but after 1 hour after “updating” Flash Player. It is located here: C:\Documents and Settings\User\LocalSettings\Temp and is “registered” in the registry section HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\WindowsNT\CurrentVersion\Winlogon. We reboot after inserting a Live CD from Dr.Web or ERD Commander 5 into the drive (the Live CD or ERD Commander 5 image is written to the disc at minimum speed, since the disk may not boot).
We launch Regedit, type userinit into the search and return it to its original state. If LiveCD does not have the ability to edit the registry, then simply go to C:\Document and Setting\User\LocalSettings\Temp and delete the banner file from there. In our case it is der1.tmp. We reboot the computer - the banner has disappeared, run Regedit, type userinit into the search and return it to its original state. Now we need to restore the system.
SMS banner with ad view counter:
When you click on “download book” or “download song” a window appears. You give permission to install your own banner. Read the “agreement”!
When you press the button Close(or by clicking on the link Remove ads) a window appears with a message that you “are required to view more... impressions of advertising mailings, or refuse to view advertising by sending an SMS with the text 7728 to number 4125”:
When installed, the virus creates in C: the virus creates folders CMedia And FieryAds, and also the file fieryads.dat
If you try to uninstall a program using a file Uninstall.exe, (there is such a file in these folders, then a window will open with a message that you obliged view 1000 more impressions of this ad:
How to eliminate this SMS banner:
1. Disconnect from the Internet and local network, close all open web pages, clear the cache of temporary Internet files saved by the web browser and delete cookies (you can do this quickly with CCleaner).
2. Since the folder \Documents and Settings\Username\Application Data\ attributes set Hidden, System, Only for reading to find and destroy viruses, then open My computer, select menu Tools –> Folder Options…(or click Start -> Settings -> Control Panel -> Folder Options);
– in the dialog box that opens Folder properties open the tab View;
- In chapter Extra options check the box Display the contents of system folders, uncheck Hide protected system files, set the switch Show hidden files and folders –> OK.
3. Unload the porn banner from memory using the utility Process Explorer or wait until his window closes on its own;
– find the folder \Documents and Settings\Name_ user\Application Data\CMedia;
– delete it with all its contents (it is possible that the files CMedia.dll And g.fla you won’t be able to delete it just like that – without rebooting; To remove them without rebooting, you will need help Process Explorer);
– find the folder \Documents and Settings\Name_ user\Application Data\FieryAds;
– delete it along with its contents (files FieryAds.dll And FieryAdsUninstall.exe);
- in folder \Documents and Settings\Name_ user\Application Data delete the file fieryads.dat.
Scan the system with Dr. Web CureIt.
The taskbar will be missing, neither the Task Manager nor anything else can be launched. The explorer.exe process is disabled. Boot into Safe Mode (F8 before Windows starts).
To restore Task Manager to work, save this line:
REGaddHKCU\
Software\
Microsoft\
Windows\
CurrentVersion\
Policies\
System
/ vDisableTaskMgr / tREG_ DWORD / d 0 / f
Boot into safe mode with command line support (there is such a boot option in the menu), Type this line and press Enter.
A message should appear indicating that the command completed successfully.
Reboot normally. Task Manager should start.
Using a similar method, you can “bring back to life” the registry editor. Regedit. To do this you need to enter this line:
REG add HKCU\Software\Microsoft\Windows\CurrentVersion\Policies\System /v DisableRegistryTools /t REG_DWORD /d 0 /f
This way you can disable all autoloading:
REG DELETE HKLM\Software\Microsoft\Windows\CurrentVersion\Run /va /f
Scan the system with Dr.Web CureIt.
P.S. If you still haven’t dealt with the virus, describe the problem in the comments, I will definitely try to help, and you can also add your problem to the article.